How to run WAF profiling
Test payload libraries against a baseline on critical paths.
Steps
- Configure the profiling path and baseline request.
- Start the run and monitor progress.
- Compare baseline vs payload outcomes.
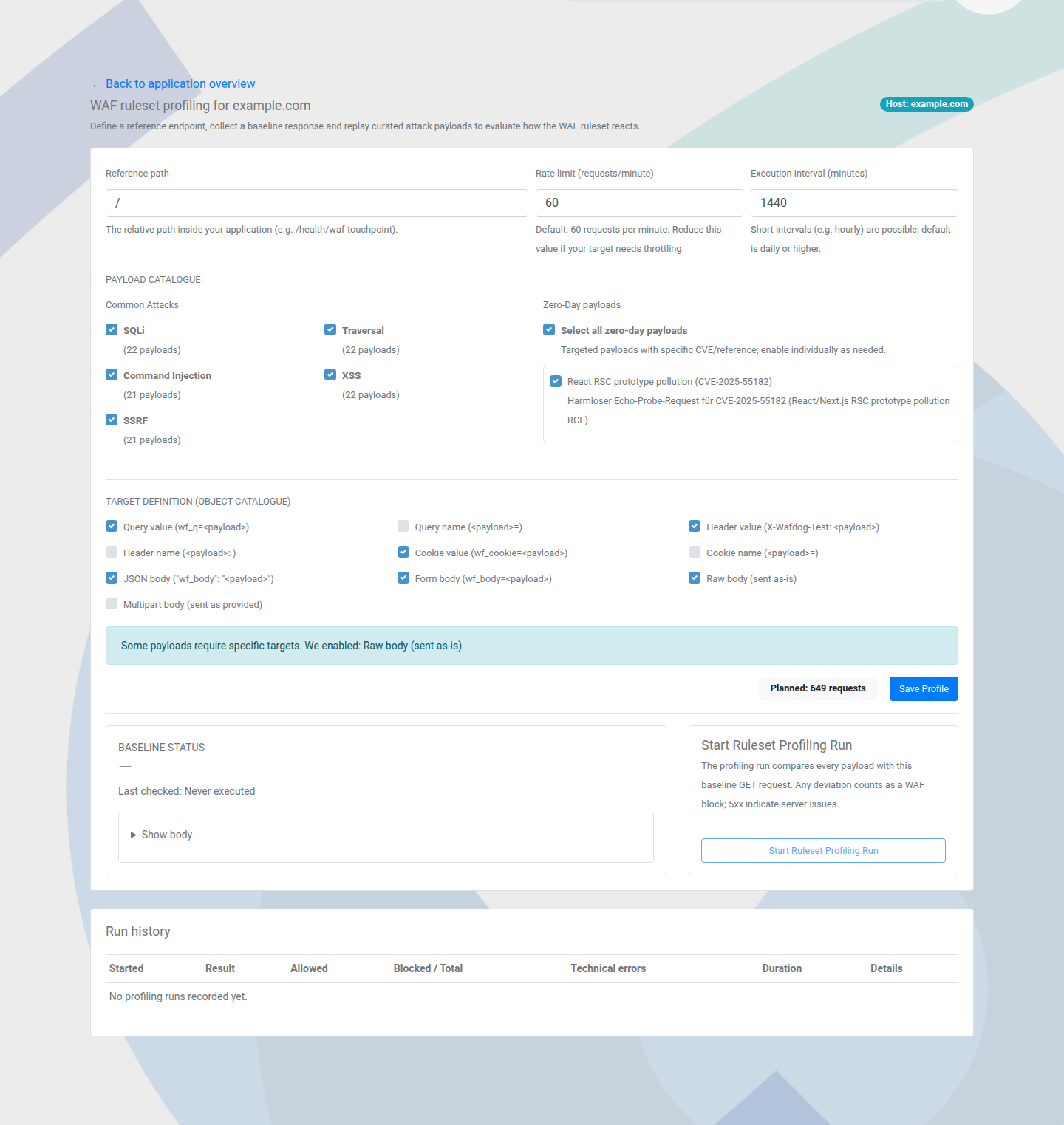
WAF profiling compares a clean baseline request against a payload catalog to reveal blocks, false positives, and regressions.
Test payload libraries against a baseline on critical paths.

Translate results into migration proof and tuning actions.
Pair WAF profiling with monitoring history and alerting to complete your evidence trail.